The Threat We Didn’t See Coming: Awakening to Threat Modeling
It started like any other digital transformation project: a multinational client, a tight deadline, and the excitement of architecting a greenfield platform in the cloud. We had microservices humming in Kubernetes, event streams flying through Kafka, and pipelines buzzing in CI/CD. Security? Of course, we had it: identity via OpenID Connect, TLS everywhere, secrets in Vault. We had checked the boxes. Or so I thought.
We were halfway through implementation when the security team ran a red team exercise. Within hours, they exploited a misconfigured API, pivoted through a vulnerable internal admin tool, and simulated exfiltrating customer data. I remember staring at the findings document, my stomach dropping. I hadn’t just missed a threat. I had missed the modeling of threats altogether.
Why Architects Overlook Threat Modeling
Despite its critical role in designing secure systems, threat modeling often gets sidelined in architecture work. Not because it’s unimportant, but because our workflows, incentives, and assumptions quietly push it to the margins. Looking back, I realize I fell into the same trap many solution architects do:
- We focus on design, not deception. Our mindset is to build, not break. That can blind us to how systems can be subverted.
- Security is often delegated. We assume the security team will "handle it", without realizing threat modeling is a design activity, not just a checklist.
- Frameworks don’t make it obvious. TOGAF, ArchiMate, even the C4 model often gloss over the threat landscape unless you explicitly add it.
We architects love patterns, but threat modeling isn’t just another pattern, it’s a total new reel on the View Master. You focus on capability or performance, you begin to see the architecture as an ecosystem of assets, actors, trust boundaries, and exposed surfaces. And here’s the uncomfortable truth: threats don’t reside inside individual components, they emerge between them. In the transitions, the integrations, the assumptions no one challenged. Once you slide in the threat model reel, you start to see risks you didn’t know were there all along.
My First Real Threat Modeling Session
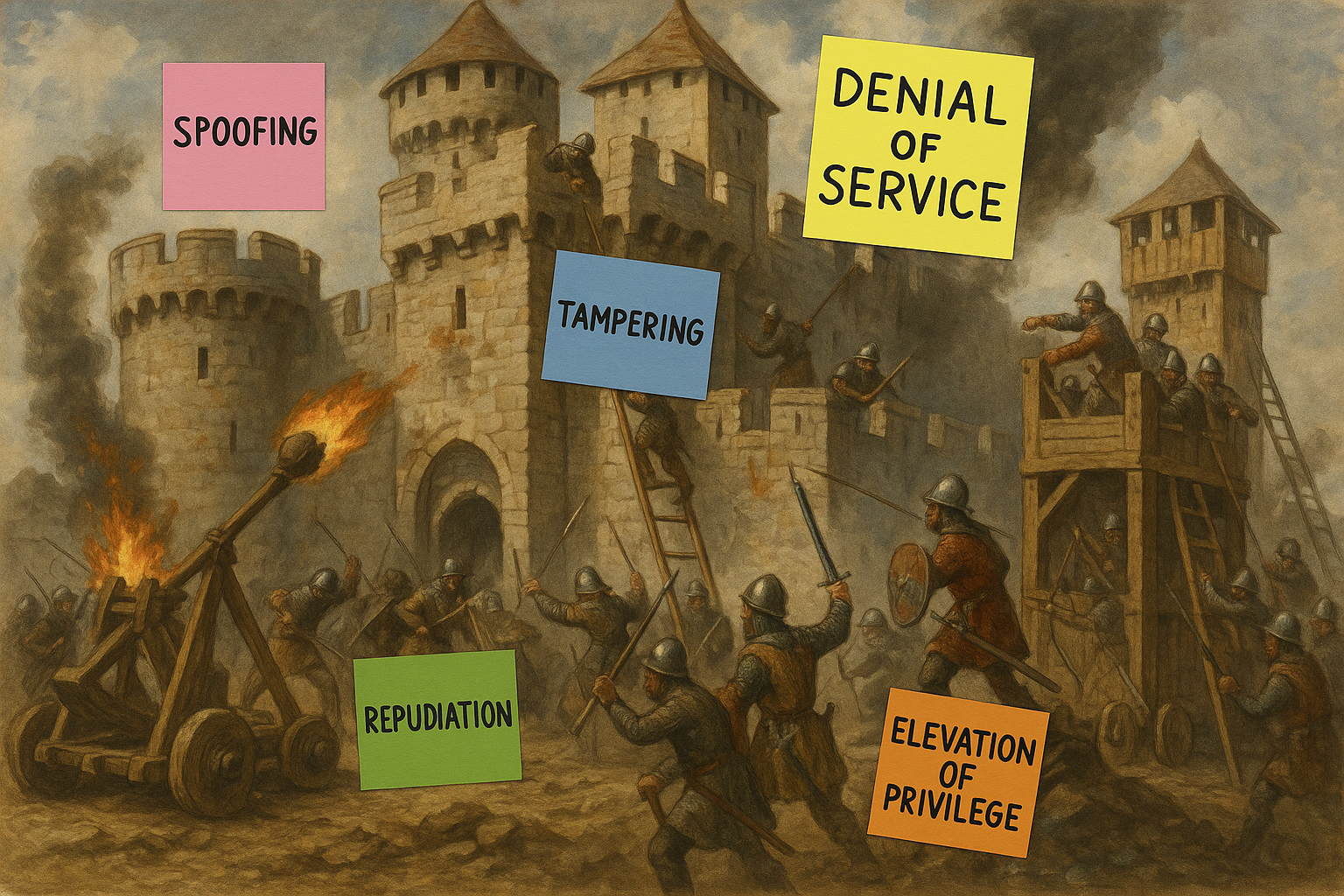
After the red team exercise exposed our blind spots, I knew we couldn’t move forward with business as usual. I needed more than just patching the flaws. We had to rethink how we designed for security from the ground up. So I called a threat modeling session, unsure of how the team would respond. Would they see it as a valuable design activity, or just more overhead in an already tight sprint? We started simple: STRIDE.
| Threat | Threat Definition |
|---|---|
| Spoofing identity | Pretending to be something or someone other than yourself |
| Tampering with data | Modifying something on disk, network, memory, or elsewhere |
| Repudiation | Claiming that you didn’t do something or were not responsible; can be honest or false |
| Information disclosure | Someone obtaining information they are not authorized to access |
| Denial of service | Exhausting resources needed to provide service |
| Elevation of privilege | Allowing someone to do something they are not authorized to do |
I ran a session with the team using our C4 diagrams as a base. We printed out the Container diagram, added Post-Its for each STRIDE category, and let engineers, testers, and even product owners poke holes in the design. It was transformative.
We discovered:
- Improper error handling could leak stack traces or backend URLs.
- No rate limiting allowing brute-force or flood attacks.
- Lack of request logging could prevent tracing malicious activity.
Even better, the team left energized. They weren’t just fixing bugs, they were defending a system. It gave the architecture purpose beyond scalability and elegance.
Embed Threat Modeling in the Architecture Lifecycle
Once I had seen the impact of that first session, how a simple shift in perspective revealed critical gaps, I couldn’t unsee it. It became obvious: threat modeling shouldn’t be a one-off workshop or security checkbox. It needed to live where architecture lives: in our lifecycle, our rituals, our decision gates. Yet this is where many teams get stuck. They want security, they want resilience, but they don’t know where threat modeling fits in the messy reality of delivery. The good news? You don’t need to overhaul your process, you just need to intentionally layer in threat modeling at the right moments, using the models you already work with.
1. Bring Threat Modeling Into Inception
Right from discovery or pre-mortem workshops, begin identifying what matters most. What are the crown jewels? Who are the users and potential abusers? Align on business-critical assets and risk tolerance before design begins. This gives threat modeling teeth because you’re anchoring it in value, not paranoia. Use simple whiteboarding or sticky-note exercises with business and tech leads to surface assumptions and risk perceptions.
2. Annotate Existing Architecture Views
Use your existing C4, flowcharts, or component diagrams. Don’t create separate “security diagrams.” Instead, overlay threats directly onto architecture views, like trust boundaries, external interfaces, and sensitive data flows. Use icons or color-coded notes to indicate STRIDE threats. Think visually. When developers see where spoofing or tampering can occur on their own components, it becomes real.
3. Facilitate, Don’t Dictate
As an architect, you don’t need to be the security expert, you need to create space for threat exploration. Run sessions where engineers, testers, and even product folks can contribute. Focus on asking the right “what if” questions:
- What happens if this token is reused?
- What if this service goes offline?
- Who could abuse this endpoint?
Tools like STRIDE, or Kill Chain work well to prompt divergent thinking.
4. Treat Threats Like Architectural Decisions
Once identified, threats should flow into the same decision-making process as any other design trade-off. Can we mitigate it? Can we accept it? Does it require a systemic change? Track them just like you would technical debt or design decisions, because that’s exactly what they are. Capture threat scenarios in an ADR (Architecture Decision Record) format with mitigation notes and ownership.
5. Revisit Regularly, Not Just at Release
Threats aren’t static. New integrations, new dependencies, and evolving business rules introduce emergent risks. Make threat modeling part of architectural reviews, roadmap updates, and even incident retrospectives. Add a threat lens to your “definition of done” for architecture epics or quarterly tech strategy reviews.
From Bolt-On to Built-In
When threat modeling becomes a natural part of your architectural rhythm, not a bolt-on, but a built-in, you unlock more than just secure systems. You empower teams to think critically, design defensively, and connect their code to real-world impact. If you’re not already threat modeling, start small. Take your most recent system diagram and ask: “Where could this fail, and who might want it to?”. Run a 30-minute session. Invite your team. Use sticky notes. Use STRIDE. Just start because every resilient architecture begins with the threats we choose to see.
Share this article
Enjoyed this article?
Subscribe to get more insights delivered to your inbox monthly
Subscribe to Newsletter